Tier your vendors by Criticality – A critical step of a vendor risk management program
A recent Ponemon study found that only 34% of companies maintain a comprehensive list of their vendors. 69% of the participants in the study blamed “a lack of centralized control” as the key factor as to why a comprehensive inventory had not been created.
Security departments must take a leading role in these situations in order to effectively manage the risks they are inherently exposed to. Vendor risk is not one-size-fits-all. Classifying vendors by Tier so you can ask relevant questions during your security review process is a critical step in the vendor risk management program lifecycle.
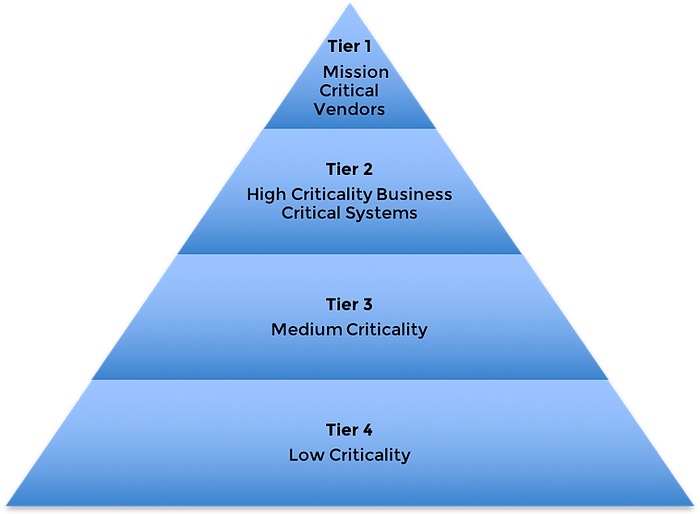
Privva has a 4-tier vendor classification system based on data access, network or physical access and business criticality.
Risk Tier 1 vendors will be classified as business and mission critical vendors that pose the greatest risk to overall security, privacy, and operations. Vendors in the tier 1 category will receive the most comprehensive advanced assessment. We expect to conduct rigorous inquiries into each of these vendors’ policies, procedures, and network architecture.
Risk Tier 2 vendors will be classified as high risk vendors. Vendors in the tier 2 category will receive a less exhaustive advanced assessment compared to the tier 1 assessment. The tier 2 assessment will still incorporate questions covering the main risk categories, but our main objective will be to identify vendors’ policies, procedures, and architecture.
Risk Tier 3 vendors will be classified as medium risk vendors. Vendors in the tier 3 category will receive a more focused advanced assessment compared to the tier 2 assessment. Even though these vendors lack the same business criticality as tier 1 and tier 2 vendors, it is still important to understand the controls in place designed to protect the company from risk.
Risk Tier 4 is an optional tier we may leverage for low tier vendors if this level of categorization is needed to maintain a full inventory of all vendors. These may include vendors that do not have access to sensitive information or connectivity to systems/networks. For example, janitorial staff may be a vendor to be inventoried on Privva but may not require an evaluation as part of the engagement.
As the definition of a vendor expands, companies need to thoughtfully review their comprehensive vendor lists. Managing third party risk is only as effective as the completeness of your assessment strategy. Make sure to consider the risks posed by all vendors within your ecosystem and develop an assessment approach to accommodate the full spectrum of these risks.
To learn more about how to centralize, control, and Tier your vendors within the Privva platform please contact us.
Share this post!
Smarsh Blog
Our internal subject matter experts and our network of external industry experts are featured with insights into the technology and industry trends that affect your electronic communications compliance initiatives. Sign up to benefit from their deep understanding, tips and best practices regarding how your company can manage compliance risk while unlocking the business value of your communications data.
Ready to enable compliant productivity?
Join the 6,500+ customers using Smarsh to drive their business forward.






Subscribe to the Smarsh Blog Digest
Subscribe to receive a monthly digest of articles exploring regulatory updates, news, trends and best practices in electronic communications capture and archiving.
Smarsh handles information you submit to Smarsh in accordance with its Privacy Policy. By clicking "submit", you consent to Smarsh processing your information and storing it in accordance with the Privacy Policy and agree to receive communications from Smarsh and its third-party partners regarding products and services that may be of interest to you. You may withdraw your consent at any time by emailing privacy@smarsh.com.
FOLLOW US